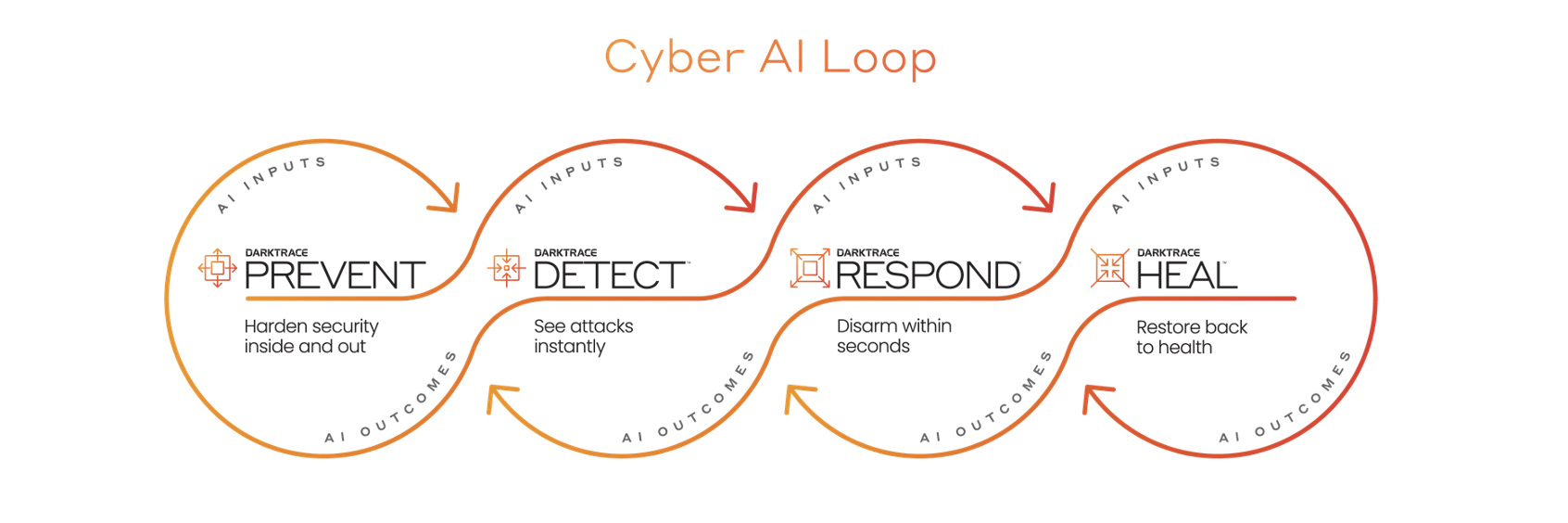
Darktrace Resources
Thank you! Your submission has been received!
Resources
Gated Video

NIS2 Directive: Implications on Cyber Security and AI
Gated Video

NIS2 Directive: Implications on Cyber Security and AI
Resources
April 16, 2024
services,managed,detect,respond
4
Data Sheet

Darktrace Services: Managed Detect + Respond (MDR)
4
services,managed,detect,respond
Data Sheet

Darktrace Services: Managed Detect + Respond (MDR)
Resources
April 9, 2024
Data Sheet

State of AI Cyber Security 2024 Infographic
Data Sheet

State of AI Cyber Security 2024 Infographic
Resources
December 12, 2023
Gated Video

BSI Lagebericht 2023 Webinar 🇩🇪
Gated Video

BSI Lagebericht 2023 Webinar 🇩🇪
Resources
February 22, 2024
3
Gated Video

Exploring the Evolving Email Security Landscape
3
Gated Video

Exploring the Evolving Email Security Landscape
Resources
April 9, 2024
Data Sheet

State of AI Cyber Security 2024 Executive Summary
Data Sheet

State of AI Cyber Security 2024 Executive Summary
Resources
March 26, 2024
3
Gated Video

Darktrace/Cloud Product Spotlight
3
Gated Video

Darktrace/Cloud Product Spotlight
Resources
April 9, 2024
2
White Paper

State of AI Cyber Security 2024
2
White Paper

State of AI Cyber Security 2024
Resources
April 10, 2024
platform, email, OT, Virtual Innovation Launch
2
Video
Darktrace Virtual Innovation Launch
2
platform, email, OT, Virtual Innovation Launch
Video

Darktrace Virtual Innovation Launch
Resources
April 9, 2024
platform
2
Data Sheet

Darktrace ActiveAI Security Platform Solution Brief
2
platform
Data Sheet

Darktrace ActiveAI Security Platform Solution Brief
Resources
April 9, 2024
OT,Darktrace/OT Solution Brief,ICS
3
Data Sheet

Darktrace/OT Solution Brief
3
OT,Darktrace/OT Solution Brief,ICS
Data Sheet

Darktrace/OT Solution Brief
Resources
April 9, 2024
email
3
Data Sheet

Darktrace/Email Solution Brief
3
email
Data Sheet

Darktrace/Email Solution Brief
Resources
March 28, 2024
5
Video
Threat Analysis Stories: Detecting Exploitations of the Ivanti Vulnerability
5
Video

Threat Analysis Stories: Detecting Exploitations of the Ivanti Vulnerability
Resources
center for internet security the 18 critical security controls
Data Sheet

Center for Internet Security: The 18 Critical Security Controls
center for internet security the 18 critical security controls
Data Sheet

Center for Internet Security: The 18 Critical Security Controls
Resources
March 15, 2024
2023 sec cybersecurity reporting requirements
Data Sheet

2023 SEC Cybersecurity Reporting Requirements
2023 sec cybersecurity reporting requirements
Data Sheet

2023 SEC Cybersecurity Reporting Requirements
Resources
March 7, 2024
5
Video
Threat Analysis Stories: Defending Against a Gootloader Malware Attack
5
Video

Threat Analysis Stories: Defending Against a Gootloader Malware Attack
Resources
March 1, 2024
5
Video
Threat Analysis Stories: Catching an Attempted Dropbox Account Takeover
5
Video

Threat Analysis Stories: Catching an Attempted Dropbox Account Takeover
Resources
March 5, 2024
Reversing the Tide: Preventing the Top 4 Supply Chain Risks in 2024,cloud,network,email,zero trust,zero-trust,prevent,detect,respond,asm,apm,supply,chain,supply chain,supply chain attacks,
4
White Paper

Reversing the Tide: Preventing the Top 4 Supply Chain Risks in 2024
4
Reversing the Tide: Preventing the Top 4 Supply Chain Risks in 2024,cloud,network,email,zero trust,zero-trust,prevent,detect,respond,asm,apm,supply,chain,supply chain,supply chain attacks,
White Paper

Reversing the Tide: Preventing the Top 4 Supply Chain Risks in 2024
Resources
March 4, 2024
ot,Darktrace+XageJointSolution
Data Sheet

Darktrace + Xage Joint Solution
ot,Darktrace+XageJointSolution
Data Sheet

Darktrace + Xage Joint Solution
Resources
February 29, 2024
ciso,stories,cloud,security
White Paper

CISO Stories: Cloud Security
ciso,stories,cloud,security
White Paper

CISO Stories: Cloud Security
Resources
February 29, 2024
AI,arms,race,ciso,stories
White Paper

CISO Stories: The AI Arms Race
AI,arms,race,ciso,stories
White Paper

CISO Stories: The AI Arms Race
Resources
February 22, 2024
trends,analysis,year,end,threat,report,pattern,intelligence,
5
White Paper
End of Year Threat Report
5
trends,analysis,year,end,threat,report,pattern,intelligence,
White Paper

End of Year Threat Report
Resources
February 15, 2024
psychology,confirmation bias,trust,stress
4
White Paper

AI with Humans in Mind
4
psychology,confirmation bias,trust,stress
White Paper

AI with Humans in Mind
Resources
February 15, 2024
security practices,implementing ai,LLM,gen ai,generative ai,ai adoption,reliable ai,
4
White Paper

Best Security Practices for Implementing AI in the Enterprise
4
security practices,implementing ai,LLM,gen ai,generative ai,ai adoption,reliable ai,
White Paper

Best Security Practices for Implementing AI in the Enterprise
Resources
February 13, 2024
ot,asset,identification,ICS
Data Sheet
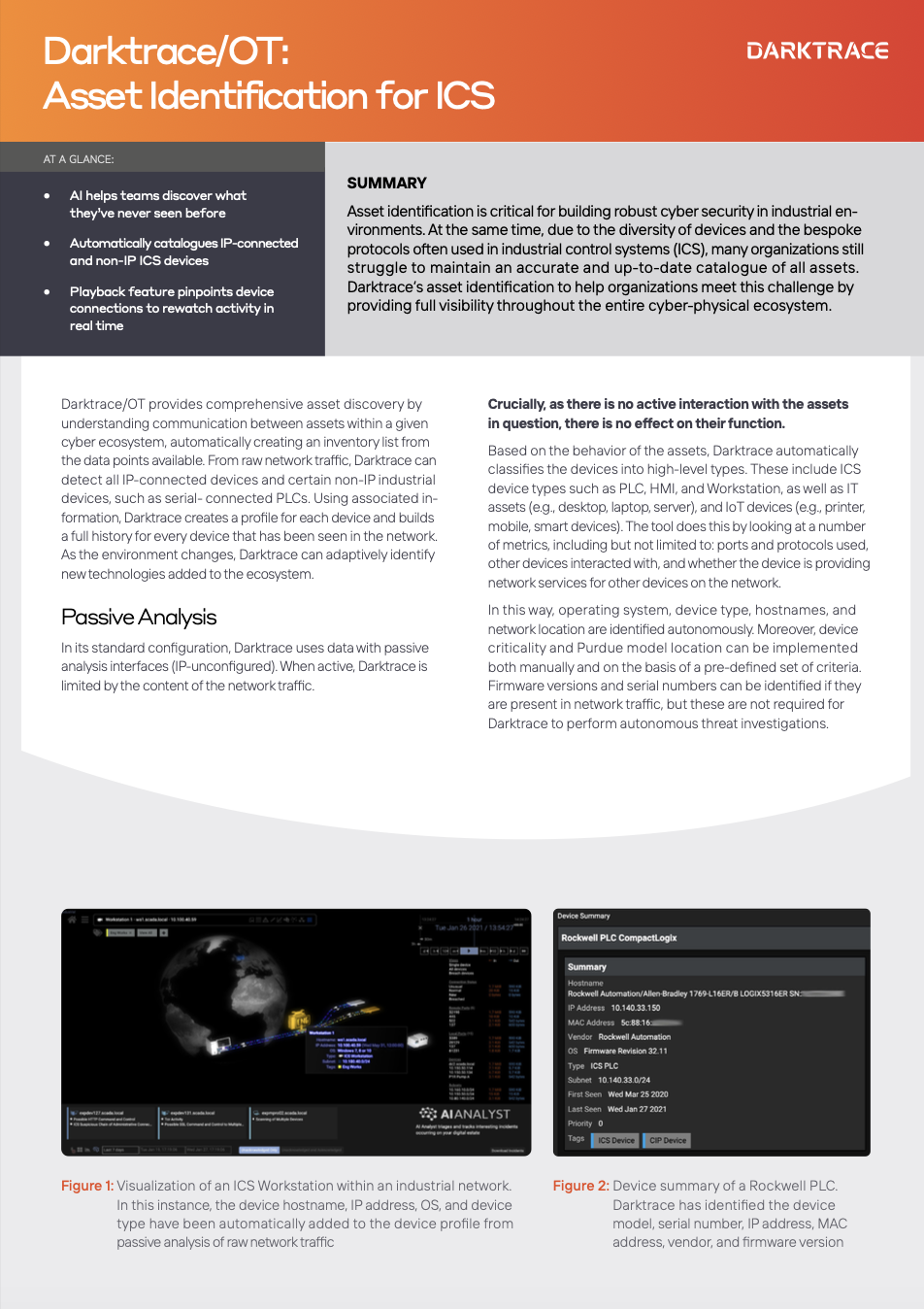
Darktrace/OT: Asset Identification for ICS
ot,asset,identification,ICS
Data Sheet

Darktrace/OT: Asset Identification for ICS
Resources
February 8, 2024
FERC,order,887,support,darktrace,ot
Data Sheet

Darktrace in Support of FERC Order 887
FERC,order,887,support,darktrace,ot
Data Sheet

Darktrace in Support of FERC Order 887
Resources
February 8, 2024
ot,integrations,digital,systems
Data Sheet

Darktrace/OT: Plugging into your Digital Systems
ot,integrations,digital,systems
Data Sheet

Darktrace/OT: Plugging into your Digital Systems
Resources
February 5, 2024
compliance,
White Paper

7 Steps to Get Ahead with NIS2
compliance,
White Paper

7 Steps to Get Ahead with NIS2
customer story


The Museum of Flight
This is some text inside of a div block.
museum of flight,network,email,apps,saas,endpoint,prevent,asm,attack surface management,heal,supply chain attacks,ip,data loss,attack simulation,playbook,play book
customer story


D24
This is some text inside of a div block.
d24,directa24,cloud,email,network,apps,saas,zero trust,payment card industry data security standard,PCI DSS,compliance
customer story
.jpg)

Australian Grand Prix
This is some text inside of a div block.
australian,grand,prix,gp
customer story


Telenor IoT
This is some text inside of a div block.
cloud,detect,cloud-transformation,technology
10
customer story


Dreamworld
This is some text inside of a div block.
hospitality,apps-microsoft-365,cloud-transformation,endpoint,cloud,detect,respond
10
customer story


Masonicare
This is some text inside of a div block.
healthcare-and-pharma,detect,respond
10
customer story


Primaflor
This is some text inside of a div block.
email,apps-microsoft-365,network,detect,respond
10
customer story


Direct Federal Credit Union
This is some text inside of a div block.
financial-services
10
customer story


American Kidney Fund
This is some text inside of a div block.
phishing,healthcare-and-pharma,cloud-transformation,nonprofit
10
customer story


Differentia Consulting Case Study
This is some text inside of a div block.
technology,apps,cloud-transformation,respond
10
customer story

Duferco Case Study
This is some text inside of a div block.
ransomware,network,manufacturing-and-supply,respond
10
customer story


KTR Systems Case Study
This is some text inside of a div block.
manufacturing-and-supply,respond,ransomware,phishing,network
10
customer story


City of Tyler Case Study
This is some text inside of a div block.
phishing,work-from-home,network,account-takeover
10
customer story


Grupo Mexicano de Seguros Case Study
This is some text inside of a div block.
government-regulations-compliance,financial-services,network,respond
10
customer story


Calligo Case Study
This is some text inside of a div block.
phishing,vendor-email-compromise,email
10
customer story

International Baccalaureate Case Study
This is some text inside of a div block.
education,ransomware,risk-compliance,respond
10
customer story


Funding Circle Case Study
This is some text inside of a div block.
detect,cloud,cloud-transformation
10
customer story


Boardriders Case Study
This is some text inside of a div block.
microsoft,network,apps-microsoft-365,respond
10
customer story


Mainstream Renewable Power Case Study
This is some text inside of a div block.
cloud-transformation,respond,utilities,microsoft,network
10
customer story


Guardsman Group Case Study
This is some text inside of a div block.
phishing,technology,respond
10
customer story

Copperbelt Energy Corporation Case Study
This is some text inside of a div block.
it-ot-convergence,respond
10
customer story


Scope Markets Case Study
This is some text inside of a div block.
network,cloud-transformation,respond,endpoint,financial-services
10
customer story

City of College Station Utilities Case Study
This is some text inside of a div block.
ot,security-awareness
10
customer story


IVAR Case Study
This is some text inside of a div block.
network,it-ot-convergence,manufacturing-and-supply
10
customer story


EV Group Case Study
This is some text inside of a div block.
network,manufacturing-and-supply,respond
10
customer story


Girton Grammar School Case Study
This is some text inside of a div block.
education,work-from-home,network
10
customer story


CordenPharma Case Study
This is some text inside of a div block.
healthcare-and-pharma,respond,data-protection,network,malicious-crypto-mining
10
customer story


City of Las Vegas Case Study
This is some text inside of a div block.
government-and-defense,respond,heal,apps,phishing,network
2
customer story


Sanabel Al-Salam Case Study
This is some text inside of a div block.
supply-chain-attack,phishing,respond
10
customer story

Greater Omaha Packing Case Study
This is some text inside of a div block.
manufacturing-and-supply,respond
10
customer story


Bank One Case Study
This is some text inside of a div block.
phishing,vendor-email-compromise,email,supply-chain-attack
10
customer story


AAA Washington Case Study
This is some text inside of a div block.
cloud-transformation,respond,endpoint,apps,microsoft,network,security-awareness
10






































.jpg)








_11zon.jpg)













.jpeg)
























.jpeg)

%20copy.png)